Clare Fleming, Director of Membership and Communications for the International Institute of Risk & Safety Management (IIRSM) highlights the importance of cybersecurity for SME owners.
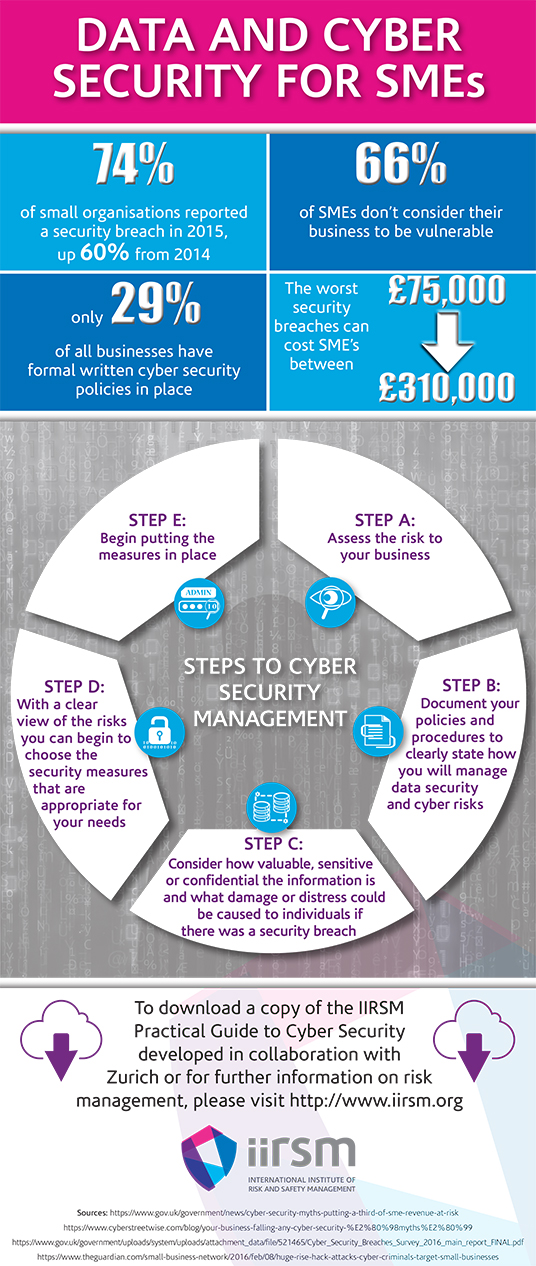
In the past year alone, 74% of small organisations reported a breach in cyber security. [1] Despite this, 66% of SMEs don’t consider their business to be at risk from an attack. [2] As the new EU Data Protection Regulation (GDPR) is set to come into force in May 2018, the International Institute of Risk and Safety Management (IIRSM) is calling for SMEs to consider how to implement effective cyber security processes.
The GDPR will require all businesses to show greater accountability and planning for their cyber security processes. It will develop existing regulations to protect and strengthen citizens’ fundamental rights and simplify the impact for business. A significant change though is that larger fines, dependant on turnover and the type of failing involved, will be incurred by businesses that breach the regulations. Therefore it will become critical for businesses to show that they have put the necessary steps in place to prevent cyber security breaches to an appropriate level.
These types of regulation changes can result in SME business owners feeling overwhelmed at the task of assessing the risks and not necessarily understanding the magnitude of the problem. In a recent survey conducted by the Government-run Cyber Streetwise campaign, just 16% said that improving their cyber security was a top priority and when asked how they put in place an effective data security protection programme, 22% admitted that they “didn’t know where to start”. [3]
The Risks Are Real
Smaller businesses are now often deemed to be easy targets as they are perceived by criminals to be less prepared and lack the plans to prevent attacks. In early 2015, a virus encrypted over 12,000 files on the company network of MNH Platinum, a vehicle hire firm based in Blackburn. It threatened the small business’s future and led to a ransom demand of £3,000 to decrypt the affected files. In an interview with The Guardian in February this year, managing director of MNH Premium, Mark Hindle said: “We were completely unprepared for a cyber breach simply due to a lack of awareness of the magnitude an attack of this type could have through mistakenly clicking a link in an email.”[4] MNH Premium were ultimately forced to pay the £3,000 demand but were lucky in being able to retrieve the documents that were crucial to the running of the business.
In the APMG International whitepaper, ‘Managing Cyber Risk’, Andrew McQuade, Managing Director of Kyngswood Services Limited explains: “The cyber activist, whether criminal, terrorist or just an individual doing it for kicks, is winning the game. In most cases this is because we are simply not prepared for the threats they can create with ease.”[5]
SMEs are regarded as lucrative to attackers as their attacks can be quick and achieve the highest return for minimum efforts. With this in mind, it is essential that reliable information is made widely available to SMEs on how and why to implement data security measures that comply with the GDPR and stop the “it will never happen to me” mentality. With knowledge and understanding of the best security plans for your business, the changes are ultimately a valuable investment that could make a huge difference when a cyber attack strikes.
Cyber Security Procedures: The Beginning
There are some simple steps that any business can take to understand the potential risks there may be and then what to do to demonstrate that everything reasonably practicable has been done to prevent a cyber attack:
Step A: Assess the risk to your business
The first step in the process is understanding exactly what is meant by personal data. Companies store a significant amount of it, both about employees, their clients or suppliers that can include dates of birth, phone numbers, addresses, email addresses and even medical records. Individually this data can form a strong starting point for somebody from outside the business to commit a breach.
Assessing the associated risks can range from identifying the potential for physical security breaches such as whether equipment containing personal data can be stolen or damaged, through to having intruder detection software in place, including firewalls, to prevent outsiders penetrating into your network online. In any case, the approach should be layered to ensure that if a tool or technique fails when you are collecting, storing, using, or disposing of data, there are other elements to maintain your protection.
Step B: Document your policies and procedures to clearly state how you will manage data security and cyber risks
Understanding the scale of the potential problem and its consequences will enable a business owner to determine how to progress; will additional help be needed from an external agency or can you produce a security plan internally that suits your needs? Developing a document showing the full business impact assessment will enable you to understand what information is obtained, processed, stored, passed to others and ultimately disposed of, as well as identify how to mitigate any breaches that could occur at either of these stages. Written procedures will give your cyber security plan clarity and a designated approach that can be followed by all employees, including keeping track of regular checks and highlighting areas of progress.
Step C: Consider how valuable, sensitive or confidential the information is and what damage or distress could be caused to individuals if there was a security breach
Having determined the various types of personal data held the next step is to evaluate the value of that data in terms of whether it is replaceable and how much it would cost to replace it. There should be assessments of the tolerance senior members of staff have towards risk – low tolerance means that senior members of staff will not tolerate any information being lost at any cost, high tolerance means that information can be lost with little impact.
Step D: With a clear view of the risks you can begin to choose the security measures that are appropriate for your needs
It may be that some levels of protection are already in place but are not being used correctly or may have holes in them. Weak links in your existing security chain can be determined by a technical assessment such as a penetration test and overcome with physical and/or administrative controls. At the forefront of ensuring that the introduction of data security procedures goes smoothly, employees should be made aware of their roles and responsibilities, particularly when a data breach occurs. The GDPR states that data breaches must be reported within 72 hours so having a clear plan of action laid out in your management system is essential along with regular tests to ensure these plans are effective.[6]
Step E: Begin putting the measures in place
At the heart of a successful cyber security plan is cultural adoption. With the support of all employees, the responsibility is divided, making the tasks smaller and more achievable. The active support of senior management members is proven to increase the chances of other staff members adopting the processes wholeheartedly. In addition, a continual flow of incentives, motivation and varied key messages will discourage staff from reverting to old ways. If this approach can demonstrate the personal impact on staff, these messages will become even stronger.
Cultural adoption will secure a firmer basis from which cyber security can become an integrated part of SME practice. When health and safety was first implemented with the launch of the Health and Safety at Work Act 1974, personal protective equipment and warning signs were new and an unusual sight for workers in industry. Today, health and safety is a normal, accepted part of working life that is implemented largely as a norm. In the same way, actions of strategic change that provide a successful cyber security plan will lead the way in cyber security becoming a norm.
Following these steps will allow you to ultimately aim for a strengthened cyber security system and plan in place that, although no system is 100% successful, should prevent a significant number of successful attacks from occurring.
While the sophistication of attacks is continually increasing, it is the remit of all employees within a SME to protect their business. With united support, it is possible for cyber security protection processes to become an ingrained mind set to the benefit of SMEs in the future.
To download the IIRSM Practical Guide or the APMG International whitepaper, please visit http://www.iirsm.org/cyber-security